One-Time Pin Flood Attacks
Share this to
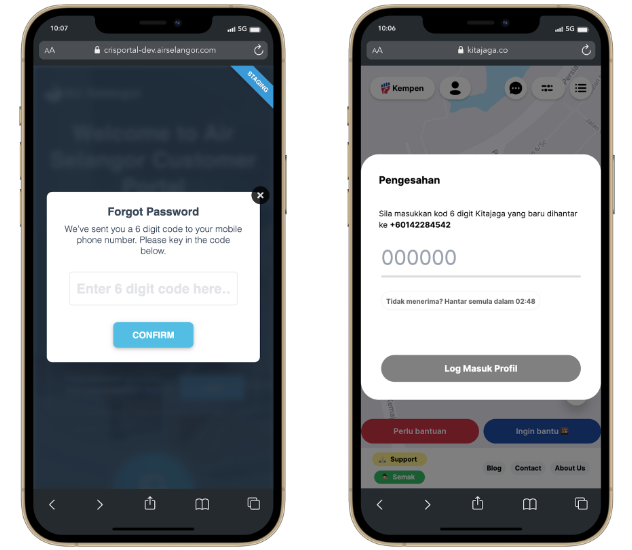
Many sites require online users to provide their cellphone number when registering in sequence for one‘s identification to be validated. During user registration, users typically press a link to send an Sms notification, and an SMS message is sent to verify the user's cell phone number. Even so, if no defense policies are in place to safeguard the SMS interface, attackers can use programs to send high-frequency demands to the SMS interface.
How does the Attack affect the Website?
First off, SMS verification consumes the website's CPU and memory, potentially resulting in poor performance. The most serious issue is that data about registered users may be leaked, endangering the company's reputation and customer base. Elaboration: Users who later attempt to log in or sign up for an account and whose phone number has already been registered as part of a flood attack may well be asked to confirm their login via email. The hacking party gets access to their email details after trying to add their email contact information to the account. The attacker can then sell your competing companies' email contact information for precision marketing purposes.
SMS flooding could also be used to aid cybercrime actions such as account hacking as well as money transfers from a vulnerable account in certain situations. Flood attacks could be used to avoid the account holder from detecting an SMS notification of bogus behavior/transaction. A dongle with a random number generator was among the first OTPs to hit the market (RNG). It displayed the very same number as the main device on the company's main server. Unfortunately, these devices were prohibitively expensive.
According to Jack Poller, an analyst at Enterprise Strategy Group, a division of TechTarget, a less expensive choice, particularly as technology advanced, was for businesses to harness the mobile phones that everyone was already carrying around. OTPs began to appear in various forms, the most common of which were passwords sent via SMS, email, or telephone conversation. However, the most commonly occurring OTP attacks nowadays are SMS Code Theft, SIM swap, and email hijacking attacks.
Making OTPs more Secure
Whereas the threat of OTP threats is not new, it is unlikely that businesses will give up OTPs anytime shortly. SMS is being phased out by UK Finance, but there are no alternative options, according to Allan. SMS OTPs were proposed for deprecation by NIST in the United States more than five years ago, but they are still in use today. OTPs could be made extra protected until a better solution is found.
One possible solution is to use timed OTP more widely (TOTP). TOTP gives users a set amount of time to enter the passcode before it expires. According to Maxim, it is an incremental gain, but it is an option to add even a little more security, which may be enough to deter some attackers.
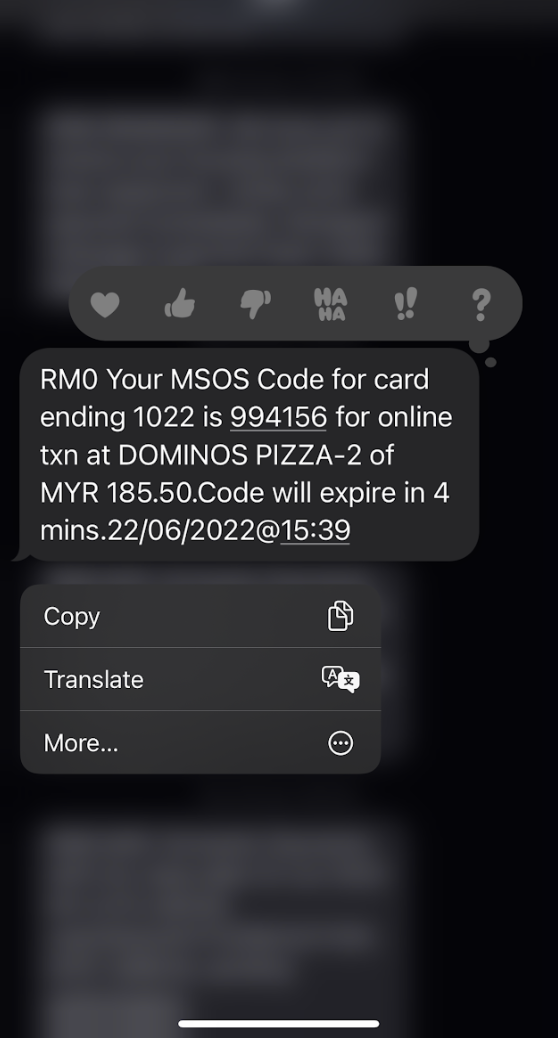 TOTP when using Online Banking
TOTP when using Online Banking
Another alternative is to use push notifications on a smartphone rather than Text messaging to send passwords or authorize login information. Push notifications are much safer than SMS using the SS7 protocol. One potential drawback of this type is pushed fatigue, which occurs when users approve access without thinking.
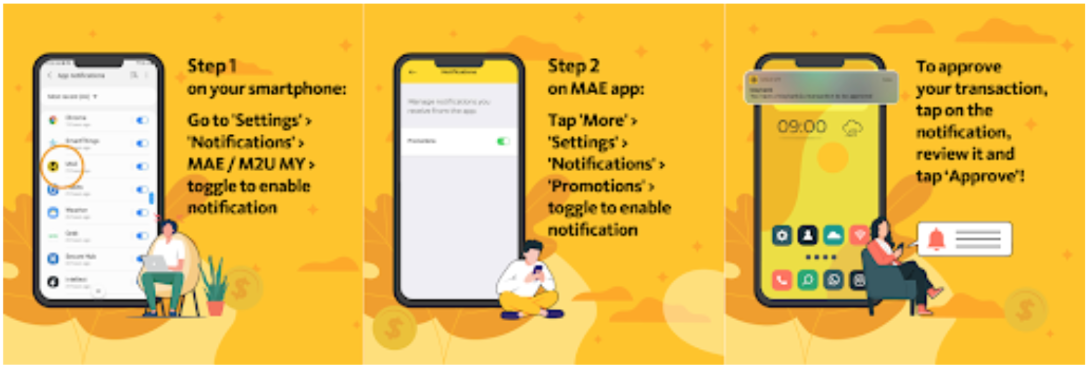 Maybank Secure2u uses Push Notifications to replace OTP
Maybank Secure2u uses Push Notifications to replace OTP
A further alternative is to return to the previous options, such as the RNG dongle. Companies could require the use of security keys from companies like Yubico and Feitian, but this choice could be costly depending on the number of workers.
Businesses could also require the use of verification apps, use push notifications that require more interaction than simply clicking OK, or collect biometric data. Companies need to consider wanting to make the OTP safer when a more safe and more user-friendly approach is implemented.
Share this to